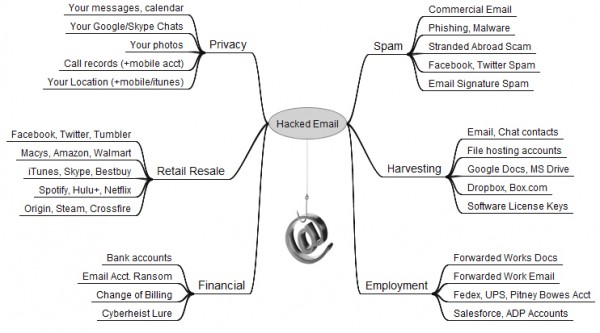
One of the most-viewed stories on this site is a blog post+graphic that I put together last year to illustrate the ways that bad guys can monetize hacked computers. But just as folks who don’t bank online or store sensitive data on their PCs often have trouble understanding why someone would want to hack into their systems, many people do not fully realize how much they have invested in their email accounts until those accounts are in the hands of cyber thieves.
This post aims to raise awareness about the street value of a hacked email account, as well as all of the people, personal data, and resources that are put at risk when users neglect to properly safeguard their inboxes.
Sign up with any service online, and it will almost certainly require you to supply an email address. In nearly all cases, the person who is in control of that address can reset the password of any associated services or accounts –merely by requesting a password reset email.
How much are these associated accounts worth? There isn’t exactly a central exchange for hacked accounts in the cybercrime underground, but recent price lists posted by several miscreants who traffic in non-financial compromised accounts offer some insights.
One prominent credential seller in the underground peddles iTunes accounts for $8, and Fedex.com, Continental.com and United.com accounts for USD $6. Groupon.com accounts fetch $5, while $4 buys hacked credentials at registrar and hosting provider Godaddy.com, as well as wireless providers Att.com, Sprint.com, Verizonwireless.com, and Tmobile.com. Active accounts at Facebook and Twitter retail for just $2.50 apiece.
As I’ve noted in previous stories, some crime shops go even lower with their prices for hacked accounts, charging between $1 to $3 for active accounts at dell.com, overstock.com, walmart.com, tesco.com, bestbuy.com and target.com, to name just a few.
Even if your email isn’t tied to online merchants, it is probably connected to other accounts you care about. Hacked email accounts are not only used to blast junk messages: They are harvested for the email addresses of your contacts, who can then be inundated with malware spam and phishing attacks. Those same contacts may even receive a message claiming you are stranded, penniless in some foreign country and asking them to wire money somewhere.
If you’ve purchased software, it’s likely that the license key to that software title is stored somewhere in your messages. Do you use online or cloud file-storage services like Dropbox, Google Drive or Microsoft Skydrive to backup or store your pictures, files and music? The key to unlocking access to those files also lies in your inbox.
If your inbox was held for ransom, would you pay to get it back? If your Webmail account gets hacked and was used as the backup account to receive password reset emails for another Webmail account, guess what? Attackers can now seize both accounts.
If you have corresponded with your financial institution via email, chances are decent that your account will eventually be used in an impersonation attempt to siphon funds from your bank account.
Until recently, some of the Web’s largest providers of online services offered little security beyond a username and password. Increasingly, however, the larger providers have moved to enabling multi-factor authentication to help users avoid account compromises. Gmail.com, Hotmail/Live.com, and Yahoo.com all now offer multi-step authentication that users can and should use to further secure their accounts. Dropbox, Facebook and Twitter also offer additional account security options beyond merely encouraging users to pick strong passwords.
Of course, all of this additional security can be defeated if the bad guys gain control over your machine through malicious software. To keep your computer from being compromised, consider adopting some of the recommendations in my Tools for a Safer PC primer.